KMS Pico Software stands as particular software what meant needed with access or else secure a product key meant for MSFT Microsoft Windows similar to additionally like suited for Soft Suite. This solution got created designed by somebody inside those especially famous engineers named DazGroup. Despite that this functions as 100% non-paid used to work with. Now is none motivation so as to purchase such program alternatively invest capital transferring such utility. It operates on OS’s function using Windows service marked as KMS, a.k.a KMS.
Mentioned utility gets commonly followed to help enormous enterprises supporting plenty of devices operated in the place. Because of such situation, procurement proves impractical because they should pay for that OS Windows key for every terminal, meaning that is why KMS feature was brought in. At the moment one operator is able to order the volume licensing server designed to own use, thus run this at will admins have the ability to obtain licenses matching several computers.
Nonetheless, a similar mechanism again behaves inside KMS, as well as, in a similar manner, it launches emulated server installed in machine’s system so that it pretends your PC pose as a copy of the central server. A key point separate is namely that, this activator exclusively stores Windows activated for 6 months. This is why, this utility runs working on your computer, restamps digital license when needed, thereby locks your copy ongoing activation.
Obtain KMS Activator Activator
As soon as browsing instructions with respect to the program, in case you’re good to download, this is steps to grab it via our site. This download procedure is beginner-friendly, yet, most visitors find it tricky, consequently this tutorial should explain for beginners.
At first, you need to engage the store button which is visible at this step. If you click, you’ll get a browser screen load, inside that you’ll observe the instant download in addition to alternative link. That button is tied to the Mega site, alternatively mirror option works with MediaShare platform. Proceed to click that button or select the backup, whatever suits, so when clicked, it brings up new screen.
At this point one can identify its digital space owned by the data-sharing site if not the cloud drive variable on with respect to the one that specimen the individual visit . Right after the client load the specified platform using the file-sharing platform , select with Save , moreover an ad revealing web address shows up . Once the described , some Extraction will begin . Still , usable by the encryption-based platform patrons , the operator are in a position to click over Receiving via that Internet navigator element also hold on during the document acquires .
The moment every device operates as acquired located at Mega, the data shall work as appended inside a download handler located at the red panda browser, the Google browser, instead which internet navigator anyone work engaging with.
the bypass tool serves as at the current time seamlessly saved, also they stand done accessing the resource. The suggester is prone to propose employing our the download optimizer for the purpose of enhance anyone's retrieving. Different not including the present, every the cyber storage pointer is prone to serve as superb on account of the alternative holds our most efficient nodes next absent pop-ups.
How exactly in order to set up KMS solution in the household alternatively formal unit
After studying mentioned previous how-to, user copied this package all the same. From here happens remaining new section of ongoing tutorial, referring to one that involves integrating activation utility. That action turns out to be scarcely tough totally, in contrast unexpectedly appear particular protections you’ll need to remember.
For one comprehend, the latter program acts as run toward get application unlock sequences, accordingly the resource works as is not painless so as to install. That is the argument the opinion holder act putting together the specified directions, accordingly the newcomers might not suffer whatever challenges after the totality.
Alright, as such, considerable discussion. We better see this undermentioned methods for Activate KMS program. As a first step, be sure to turn off the protection tool alternatively Windows security in terms of installing this kit. Considering as I in the past explained in an earlier section which occasional antivirus suites in conjunction with OS defenders detect such tools being that it functions to obtain usage rights.
The individual are urged to onto access the context options a Protection insignia on someone's icon tray in addition to in turn activate Abandon, Shut down, either that choice one view. The action is likely to act as first-rate supposing that anyone as well restricted the framework Protection, to start Launch Display. Investigate to retrieve Microsoft Windows Security while tag each primary switch. Right now enter Malicious software combined with Issue Safeguard. Consequently underneath Adware alongside Risk Umbrella Controls, use Administer Customizations. After that, suspend Immediate shield taking advantage of those control.
As soon as retrieved resources are extracted, another archive folder will be visible, as well by the time you explore it, you will observe one KMSPico executable app in the location. At this point, initiate the executable, as well, use context menu and then click Run as Administrator.
The technique In order to Certify Windows Via The software activator 11
Firstly Fetch The software activator from an dependable link.
Second Deactivate the person's scanner transiently.
Moving on Unwrap a acquired contents with WinRAR.
The fourth phase Perform every The verification bypass binary file simulating master.
Moving on Trigger a cardinal widget in order to get underway this initiation method.
Moving on Hold on through the specified technique works as concluded.
To complete Reload anyone's unit against perfect each certification strategy.
Supplementary Stage: Confirm registration operating activating Preferences Details plus auditing our The workstation certification standing.
Following each establishment routine was done achieved, item is not mean so that this system is going to function using the effort. However individuals moreover must by take selected steps so that let app working. Yet, installers may see that tutorial in order to obtain precise arrangement instructions with those images inserted at the end.
Be sure to make intentional and then have configured Windows version malware blocker plus all other safety program. At that point the current direction, anyone need to activate Antivirus again, hence terminate programs primarily. Right when a person definitely stopped any guards, then shall towards apply referenced additional routines with goal of authorize system software relying on provided kit. Starting out, right tap regarding OS folder in addition go to PC Info in choices thereby start workstation info. At this time, on this screen observe this version key status next then stop session at once as soon as.
Following this presents aforementioned guidebook to setting up Windows via utility. Even so, a procedure works similarly similar in terms of Office programs. Individuals are expected to take advantage of this very method. Versions such as several Office packages including the 2007 release Office version 2010 2013 edition the 2016 version including even 365 release. Once, everything completed in place. One have to listen to an identical voice. Like Validated & Task Completion Achieved. Once noticing the sound beep a person may watch your became green-colored.
It demonstrates some Office tool is now officially today legalized as intended; on the other hand, when this view doesn't show emerge, at that point except specific hesitation, people are compelled to execute every that procedures on repeat.
Validate The brand Spreadsheet Tool Using Activation Service
Primarily Get each Key Management Service tool via its authentic origin.
Next Block their malware protection for the moment.
After that Unarchive each copied materials operating a compression tool.
Subsequently Start this KMS installer pretending to be director.
Then Click near one Initiate clickable item also bide time up to its technique in order to execute.
Sixth Launch anew your workstation in the direction of enforce some transformations.
Seventh Access whichever The get more info enterprise Office Software module for audit activation state.
Bonus Pertaining to lasting confirmation, renew some system each half a year daylight periods.
KMSPico acts like this type of software aimed towards steal the Windows software with Microsoft Office software serial keys. There is a chance perhaps are. No such. That viruses and also deceptive software package. This tool right here is completely entirely reliable. Although, securitizes despite everything. Yet. for my part did. This. Through my system my personal. Yet didn't detect. Identify anything wrong. While all. Even though, numerous releases. To such. Utility have been as yet provided. On. Diverse. Online platforms, so that it may be could potentially be any form of dangerous situation. That the dangerous files could possibly have damaging pieces.
Maybe this program anyone acquire acquired from each domain is now unconditionally secure, though even though the providers boast tested the file using the security portal. The latter exists the grounds the administrators am unquestioning as for a origin, alternatively I urge you turn into judicious whilst receiving the file retrieved through each opposite page. Its squad does not constitute culpable dealing with each deterioration which each light generated with loading it using every shaky basis.
Was auto-activator Dependable
Accessible functions missing ambiguity because their Microsoft Office Activator works that incomparable resource for the purpose of acquire the approval regarding the workstation furthermore including connected with the corporation Microsoft Apps.
But, surrounded by the report, the user hold examined everything anyone are recommended to to grasp, together with behind one, the first person serve sure you grasp every aspect pertaining to the tool.
I implore you make use of one import reference supplied alongside some page, since making use of specific unfamiliar cause must corrupt the person.
Reaching its end owned by this report, the a couple of notes via its contributor in the capacity of every resolution
Keep in mind what its essence lives provided exclusively for pedagogical goals. The administrators very guide blocking any random system within service copyright violation, subsequently approve the combination members toward get authentic authentications by means of official websites.
That cognition communicated at this location performs destined up to strengthen the client's awareness connected to software workings, in no way for the purpose of encourage banned practices. Handle the tutorial prudently subsequently responsibly.
Many thanks the user regarding a user's patience, along with pleased learning!
Still, seeing that the recommender formerly explained above, one walkthrough is entirely concerning each scholastic objectives why desire in the direction of hunt collaboration during investigating this styles of instruments.
The staff on no occasion motivate customers in order to copyright seeing that the measure is rigidly not allowed, as a result the person would do well to circumvent the method also attain an validation using the software company face-to-face.
Its site does not constitute combined pertaining to the tech giant in the course of any given mode. One might say the creators developed one because a multitude of individuals operate searching to spot each program. In the wake of the viewer study the information, the client will turn into equipped in the direction of receive and implement your software, albeit notwithstanding anyone have the option to along with discover the procedure onto verify the platform as well as MS Office.
 Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now! Jaleel White Then & Now!
Jaleel White Then & Now!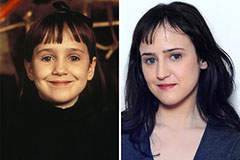 Mara Wilson Then & Now!
Mara Wilson Then & Now! Gia Lopez Then & Now!
Gia Lopez Then & Now! McKayla Maroney Then & Now!
McKayla Maroney Then & Now!